CMMC 2.0: The impact of CMMC
Regulatory requirements of DFARS 252.204-7012, 7019 and 7020
DFARS 252.204-7012 “Safeguarding Covered Defense Information (CDI) and Cyber Incident Reporting” came into effect on the 31st December 2017, and is a current (2022) regulatory requirement. It requires DoD contractors and subcontractors globally affected by DFARS 252.204-7012 to provide “adequate security” for covered defense information that is processed, stored, or transmitted on the contractor’s internal information system or network. DFARS 252.204-7012 requires that contractors implement NIST SP 800-171 to protect systems and networks that process, store, or transmit “covered defense information” and protect ‘Controlled Unclassified Information (CUI)’. The clause requires contractors to ‘flow down’ the requirements of for the implementation of the 110 NIST SP 800-171 cybersecurity practices, for the protection of Controlled Unclassified Information (CUI) and incident reporting.
In November 2020 the DoD DFARS interim rule 2019-D041 added DFARS clauses 252.204-7019, 7020 and 7021 to provide the mechanism for the DoD to oversight and assure compliance to NIST SP 800-171, to enable the DoD protect the war fighter. DFARS 252.204-7012, 7019, 7020 and 7021 have global reach, and have a direct economic impact on the DIB and the countries in which they are located. Through contractual flow-down of DFARS 252.204-7012 and prior to DoD contractor award DFARS 7019 and 7020 require.
- Contractors and subcontractors impacted by DFARS 252.204-7012, and that process CUI complete a ‘basic’ assessment of their NIST SP 800-171 compliance. They are required to submit their assessment to the DoD Supplier Performance Risk System (SPRS), before a new contract is awarded.
- Contractors are to confirm that applicable subcontractors have completed an assessment of NIST SP 800-171 compliance and submitted their scores into SPRS, prior to awarding a subcontract or other contractual instrument.
- Contractors and subcontractors should prepare for a ‘Medium’ and ‘high’ level assessments of compliance with NIST SP 800-171. To be carried out by DoD personnel, including a relevant programme office and the DCMA remotely or on site.
- Contractors and subcontractors to use the DoD assessment methodology (DAM) to assess NIST SP 800-171 compliance in accordance with NIST SP 800-171A.
DFARS 252.204-7019 requires both contractors and subcontractors to provide a summary score of their compliance to NIST SP 800-171 to the DoD Supplier Performance Risk System (SPRS) before a contract or subcontract can be awarded. Failure to do so could result in contractual penalties for a material breach of their contractual commitments, reaffirmed by the DoD in a memo released on the 16th June 2022.
In November 2020 the DoD Introduced DFARS 252.204-7021 outlining the requirements for CMMC certification to be added to DoD designated contracts. In November 2021 the DoD updated its CMMC plans, issuing CMMC 2.0. The DoD aims to add CMMC cybersecurity requirements to the contracts of DoD weapon systems and services from 2023.
Impact of CMMC 2.0 legislation
There is no confirmed date for when CMMC 2.0 will be formalized and added to DoD contracts, although the DoD has announced that it expect this to be from March 2023. Although CMMC was accommodated by the DoD in November 2020 and updated to CMMC 2.0 in November 2021, it does not replace DFARS 252.204-7012, 7019 or 7020, these clauses remain in place.
When implemented DFARS 252.204-7021 will require defence contractors and subcontractors to provide the DoD with confirmation that their cybersecurity compliance has been appropriate assessed to the DoD defined Level 1, Level 2 or Level 3. Before a contract or subcontract can be awarded.
CMMC 2.0 defines 3 levels of cybersecurity compliance, Level 1, 2 and 3.
- CMMC 2.0 Level 1 “Foundational” contractors will be required to comply to 17 “basic cyber hygiene” security practices from NIST SP 800-171 and will not require a certificate of compliance. Level 1 impacts organizations that only handle Federal Contract Information (FCI) and it removes assessment cost for organizations that do not maintain CUI. But an annual self-assessment of network practices in accordance with the basic NIST SP 800-171 requirements will be sufficient to ensure compliance. Contractors maintaining Level 1 certification will be required to assess their compliance to the 17 cybersecurity practices and upload into the DoD Supplier Performance Risk System (SPRS).
- CMMC 2.0 Level 2 “Advanced” certification will require affected organisations to adhere NIST SP 800-171 security controls. Level 2 certification will be split into two subgroups based on the level of criticality of the information possessed by the contractor. Contractors who hold CUI consisting of “Critical National Security Information” will be required to undergo third-party assessments every three years and select programs will be allowed to demonstrate compliance through self-assessments.
- CMMC 2.0 Level 3 “Expert”, which parallels the original CMMC’s 1.0 Level 5, consists of contractors who hold CUI and are involved with the “highest priority, most critical defense programs.” Contractors holding Level 3 certification will be required to comply with more than 110 practices based on NIST 800-172. The DoD will conduct its own Level 3 assessments, likely to be completed by the Defence Contract Management Agency (DCMA) every three years.
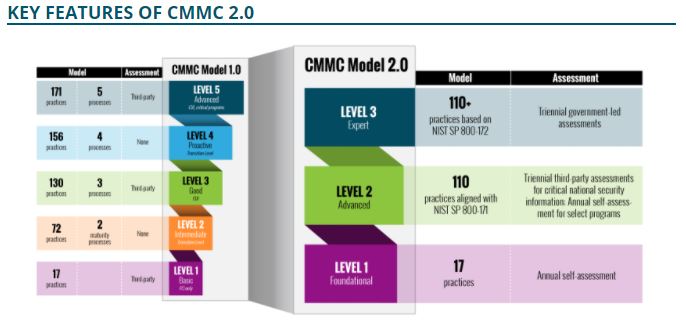
Figure 2.0: CMMC 2.0 levels and practices





