CMMC 2.0: A consistent cybersecurity framework
Cybersecurity Maturity Model Certification 2.0 – Framework
In November 2021, the Department announced “CMMC 2.0,” an updated program structure and requirements designed to achieve the primary goals of its internal CMMC review:
- Safeguard sensitive information to enable and protect the war-fighter.
- Dynamically enhance DIB cybersecurity to meet evolving threats.
- Ensure accountability while minimizing barriers to compliance with DoD requirements.
- Contribute towards instilling a collaborative culture of cybersecurity and cyber resilience.
- Maintain public trust through high professional and ethical standards.
CMMC 2.0 has been changed significantly from CMMC 1.0. The number of levels has been reduced from 5 in CMMC Level 1.0 to 3 and CMMC maturity assessments have been removed completely. CMMC 2.0 relies upon NIST SP 800-171 as required by DFARS 252.204-7012 for CMMC level 1 and 2, adding controls from NIST SP 800-172 for CMMC level 3. NIST SP 800-171 is built of security domains, practices and processes and when combined with organisational capabilities they build best practice for the protection of CUI and FCI.
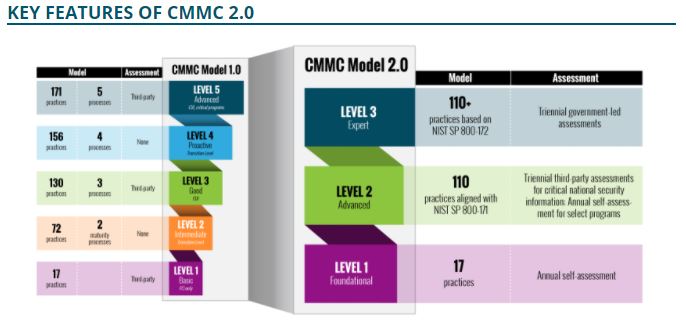
Figure 1: CMMC 2.0: Cyber security practices and NIST SP 800-171 and NIST SP 800-172 per CMMC level
CMMC 2.0 Cyber domains
The CMMC 2.0 framework consist of 14 cyber security domains, 3 fewer than CMMC 1.0. A domain is a distinct group of security practices which have similar attributes to each other and are key to the protection of FCI and CUI, either individually or in combination. The following table outlines the domains defined in the CMMC for the protection of FCI and CUI within the CMMC framework.
Table 1: CMMC 2.0 (NIST SP 800-171) Domains
Practices
In total at Level 3 the CMMC 2.0 framework identifies 110 practices, associated with the 14 security domains. 17 practices applied at maturity level 1 are referenced from FAR 52.204-21 for the basic safeguarding of covered contractor information systems applied to the protection of Federal Control Information (FCI). The 110 Practices applied at level 2 are referenced from DFARS 252.204-7012 for the safeguarding of covered defence information and cyber Incident reporting. +110 practices at Level 3 include those from NIST SP 800-171 and additional practices included from NIST SP 800-172, that are yet to be agreed.
Capabilities
Capabilities were explicitly referenced in CMMC 1.0 and removed from CMMC 2.0. However for organisations to effectively embed cybersecurity into their organisations risk management practices, strategy and operations they should be considered. Therefore we have not removed them.
Each NIST SP 800-171 domain comprises several capabilities which an organisation should aim to achieve, to ensure that cyber security and the protection of FCI and CUI is sustainable. Capabilities are a combination of practices, processes, skills, knowledge, tools and behaviors, when working together enable an organisation to protect FCI and CUI.
| C001 Establish system access requirements | C002 Control internal system access | C003 Control remote system access | C004 Limit data access to authorized users and processes | C005 Identify and document assets |
| C006 Manage asset inventory | C007 Define audit requirements | C008 Perform auditing | C009 Identify and protect audit information | C010 Review and manage audit logs |
| C011 Conduct security awareness activities | C012 Conduct training | C013 Establish configuration baselines | C014 Perform configuration and change management | C015 Grant access to authenticated entities |
| C016 Plan incident response | C017 Detect and report events | C018 Develop and implement a response to a declared incident | C019 Perform post incident reviews | C020 Test incident response |
| C021 Manage maintenance | C022 Identify and mark media | C023 Protect and control media | C024 Sanitize media | C025 Protect media during transport |
| C026 Screen personnel | C027 Protect federal contract information during personnel actions | C028 Limit physical access | C029 Manage back-ups | C030 Manage information security continuity |
| C031 Identify and evaluate risk | C032 Manage risk | C033 Manage supply chain risk | C034 Develop and manage a system security plan | C035 Define and manage controls |
| C036 Perform code reviews | C037 Implement threat monitoring | C038 Define security requirements for systems and communications | C039 Control communications at system boundaries | C040 Identify and manage information system flaws |
| C041 Identify malicious content | C042 Perform network and system monitoring | C043 Implement advanced email protections |
Table 2: CMMC Capabilities
 |  |  |  |  |  |